Warning: This software on this page is no longer supported
![]()
Overview
Port Spy is a port monitoring application that allows you to see exactly what is being transferred to and from a TCP/IP port.
The only thing you need is the capability to configure the port of either client or server to be able to insert Port Spy in between.
Port Spy is a so called “man-in-the-middle” observer. The client is no longer connected to the server, but to Port Spy. Port Spy connects itself to the server. Data received from the client is transferred -unaltered- to the server, and data replied by the server is transferred -unaltered- to the client.
There is one caveat however: While Port Spy does not change the data itself, it may change the blocking of the data. That is the grouping of data into blocks of bytes. Since blocking is a dynamic aspect of TCP/IP over which applications have no control, the client & server will be subject to this phenomenon anyhow. Even without Port Spy blocking can be different in each session.
The blocks shown by Port Spy are the blocks as they are received from either client or server.
If you develop TCP/IP software, you need a utility like Port Spy.
And just in case you need a leg up on socket programming in Swift, Port Spy comes complete with source code. Yes you read that correctly: Port Spy includes Source Code. Select “File -> Export Source Code” to obtain the Xcode project that was used to create Port Spy with all sources and even the artwork.
So not only do you get a fully functional utility, you also get to see first hand just exactly how it was made.
Features
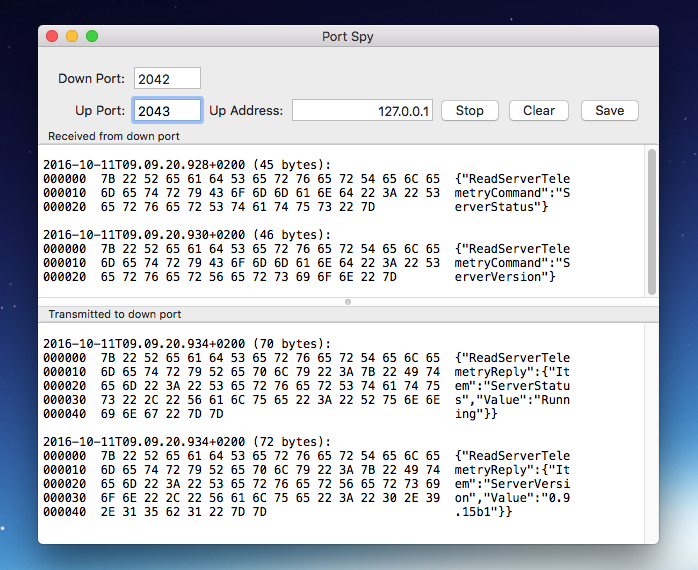
- Routes data from one port (the down-port or client) to another port (the up-port or server).
- Shows the data being transfered between down and up ports in Hex and ASCII.
- Can save the observed data to a file.
- Can handle multiple data streams (client/server connections) at the same time.
- Remembers previous sessions.
- Maintains a list of ‘Recent’ connections.
- Complete with source code:
- Shows how to do socket programming in Swift
- Contains logging utility (SwifterLog)
- Contains JSON framework (SwifterJSON)
- Contains Socket utilities (SwifterSockets)
- You are free to use the source code for your own projects (including commercial)
- No redistribution of the source allowed.
Use / User Manual
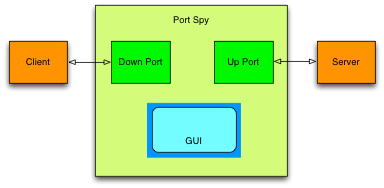
Port Spy is easy to use, just remember that it should go in between the client and server of the connection which data you want to observe.
In a picture, it looks as follows:
Local Server:
Assuming the server runs on the same computer as Port Spy and that the server listens on port 2042:
- Configure the server to listen on a different port, say 2043.
- Start Port Spy
- Create a new Port Spy window (⌘-N)
- Enter “2042” in the ‘down port’ field (the port the client needs to connect to)
- Enter “2043” in the ‘up port’ field (the port the server listens on)
- Click the ‘start’ button.
Now start the client and let it connect -as before- to port 2042. Initiate a transmission and observe the results:
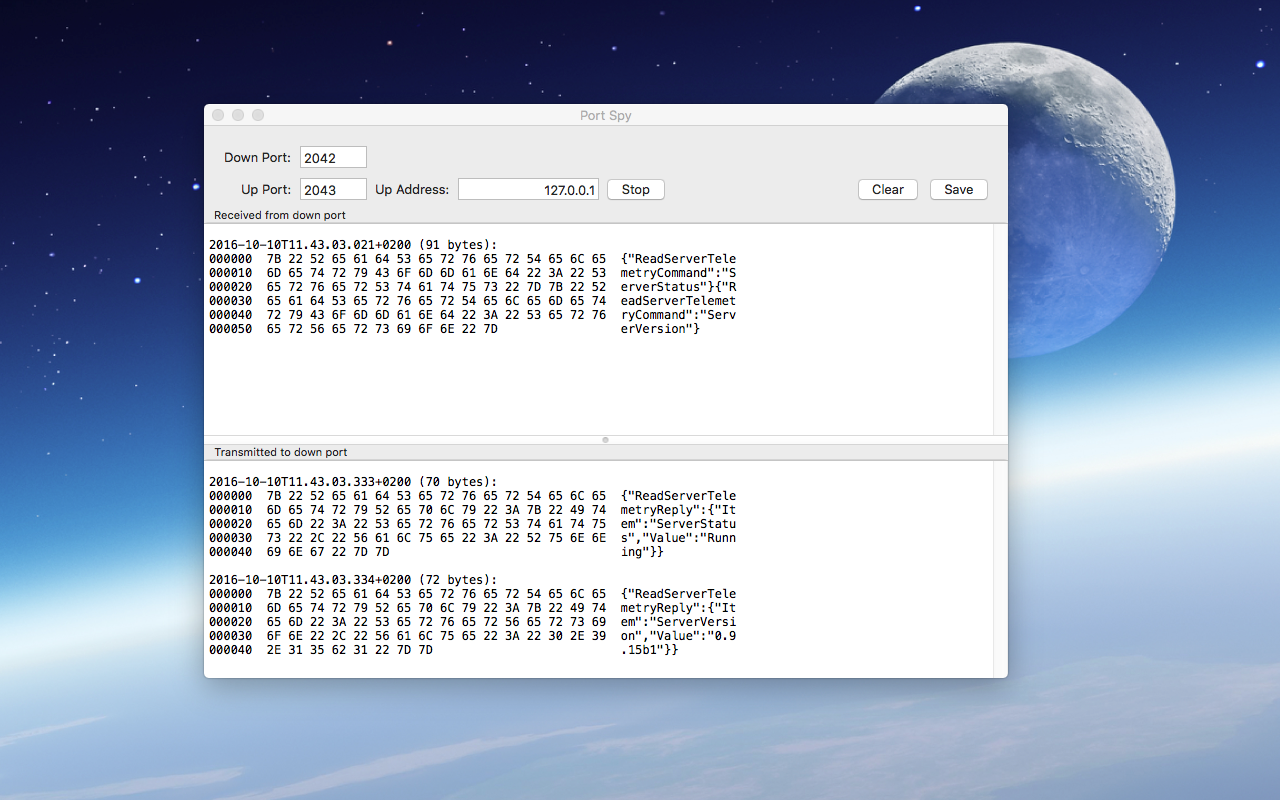
In the above example the client may run on the same computer or not.
Remote Server:
If on the other hand the client runs on the same computer and the server runs on a remote computer the setup is a little different. Now it is not possible to change the port on which the server listens. But Port Spy can be used as a local “proxy” for the remote server:
- Start Port Spy.
- Enter a free port number in the ‘down port’, say 2044.
- Enter the port number and address of the server, in the example below: port “80” on the server “balancingrock.nl”
- Start Port Spy
Now start the client and connect it to “localhost:2044” instead of “balancingrock:80” and observe the results:
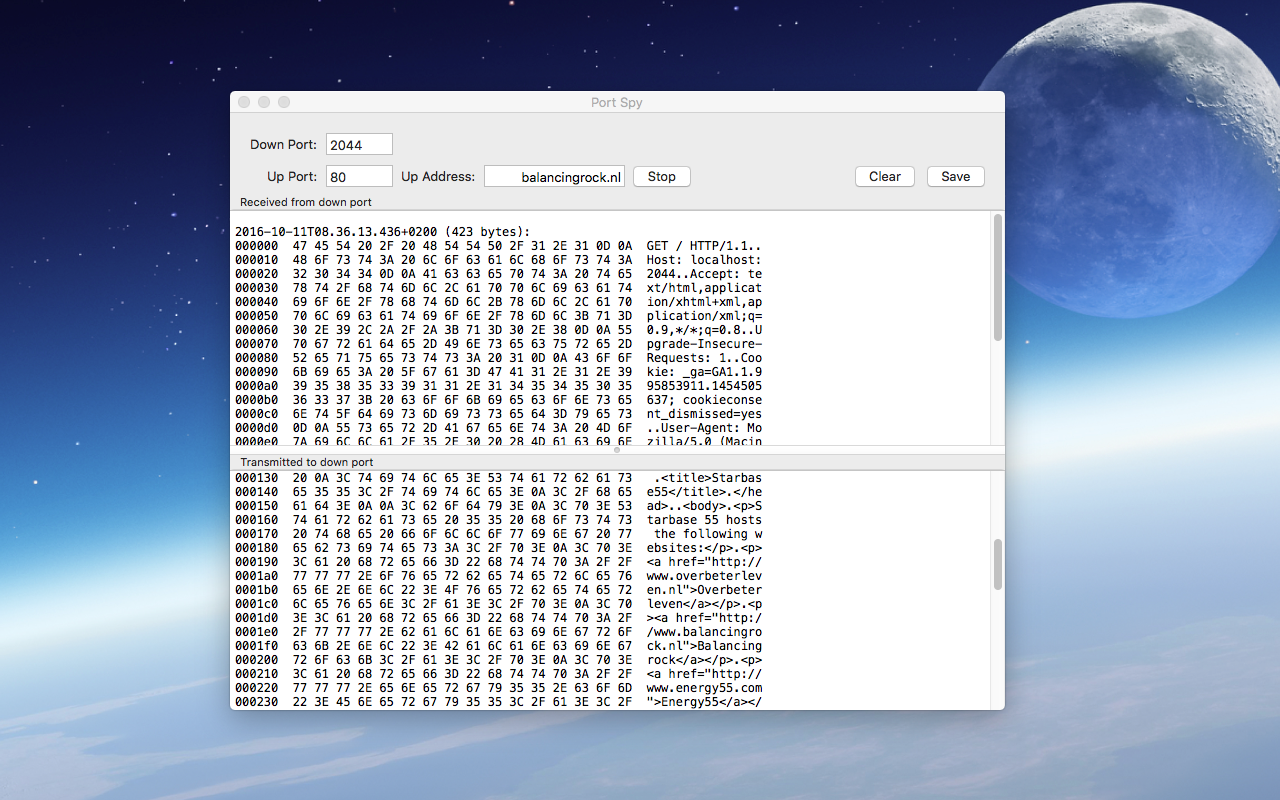
Caveat: In the above example a browser is used as a client. This creates an error since the URL must be specified as “localhost:2044”. But that means that the HTTP request contains “localhost” in its HOST field. The server at balancingrock.nl is expecting “balancingrock.nl” in the HOST field. Hence an error occurs. The error is of course visible in the byte stream, thus as an example this works fine.
